How to Access the Dark Web Safely: A 2026 Beginner’s Guide
You’ve probably heard that Tor makes you anonymous on the dark web — but that’s only half true. If you don’t use the right tools or settings, your ISP can still flag your connection. And once you’re inside, one wrong click on a fake .onion site can expose your identity or infect your device with malware.
This guide breaks down exactly how to access the dark web without putting yourself at risk. You’ll learn how to set up Tor Browser the right way, spot legit .onion links, and follow key safety checks to stay private. Whether you’re here out of curiosity or necessity, these steps will help you browse without getting burned. Editor’s Note: We value our relationship with our readers, and we strive to earn your trust through transparency and integrity. We are in the same ownership group as some of the industry-leading products reviewed on this site: ExpressVPN, CyberGhost, Private Internet Access, and Intego. That said, our detailed reviews follow a strict methodology that examines all relevant performance factors to help you arrive at your own informed conclusion.
Quick Guide: Access the Dark Web Safely in 3 Steps
- Get a reliable VPN. Pick a nearby server and enable the kill switch and DNS leak protection. If your network blocks Tor, switch to obfuscated servers for stealth access.
- Download Tor Browser from the official site. Install it on a desktop, not mobile, and set the Security Level to Safer for better protection.
- Open Tor after your VPN is connected. Stick to verified .onion sites, and never log in to personal accounts or download unknown files.
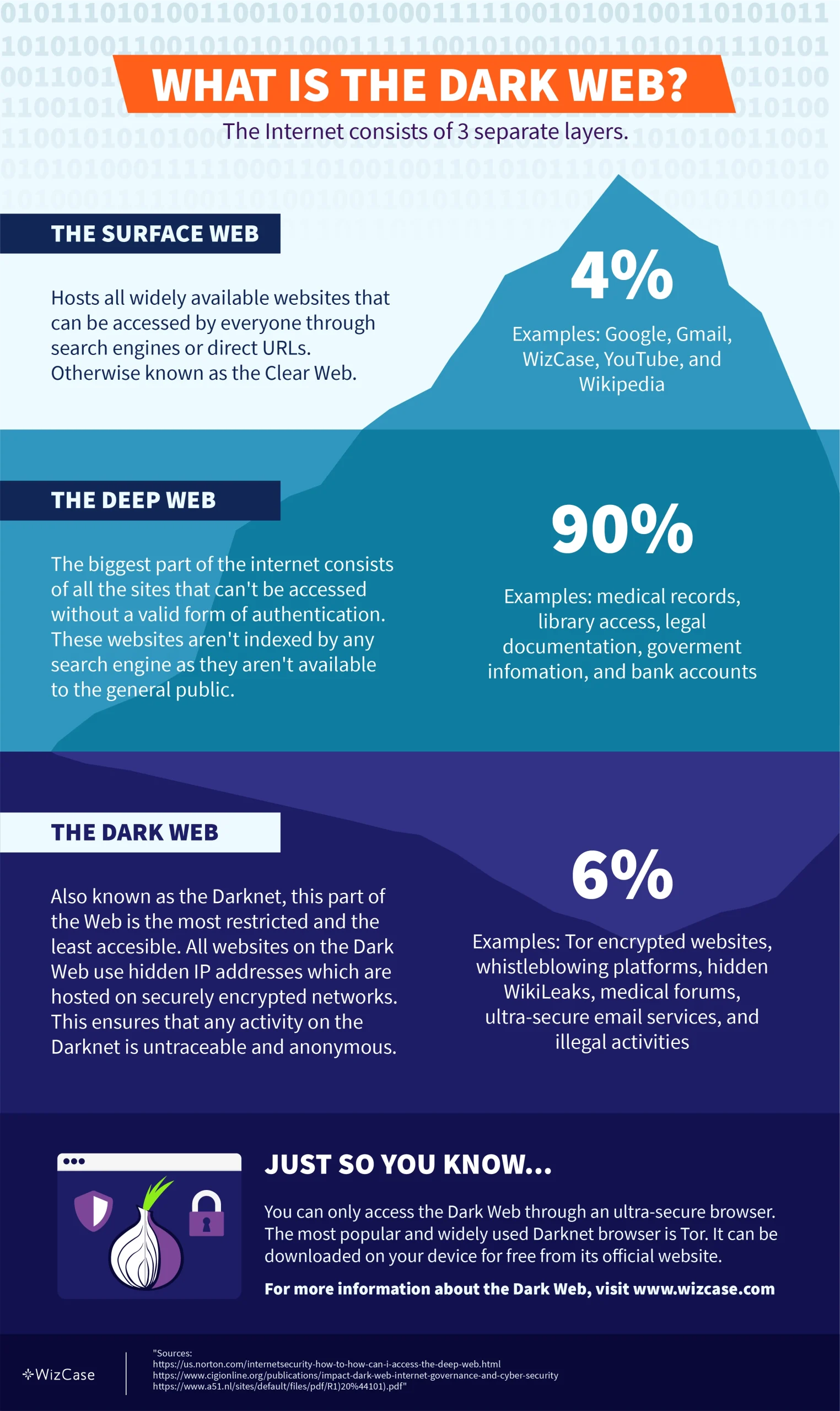
What Is the Dark Web?
The internet you use daily is just the surface. Underneath it are deeper layers that aren’t visible through normal browsing.
The Surface Web
The surface web is what you access with Chrome, Firefox, or Safari. It includes public websites like Wikipedia, YouTube, Amazon, and social media — anything that’s indexed by search engines like Google or Bing. These pages are open to everyone and don’t require any special tools to access.
The Deep Web
The deep web refers to anything that search engines can’t crawl.1 These pages aren’t public — not because they’re illegal, but because they require a login or special access. Think of your email inbox, banking dashboard, cloud documents, subscription content, or internal business tools. They’re part of the internet, but hidden from public search.
The Dark Web
The dark web is a small part of the deep web that’s only accessible through specialized tools.2 It’s home to websites that run on hidden servers called onion services, and they’re not accessible through normal browsers. You’ll know you’re on the dark web when the URLs end in “.onion” — these addresses only work inside the Tor network.
Tor routes your traffic through a chain of relays to obscure your IP address. This makes it harder for websites, ISPs, or surveillance tools to see who you are or what you’re doing. But that anonymity can also attract bad actors. Many sites on the dark web are scams, and some host illegal content.
Step-by-Step Guide: Access the Dark Web on Any Device
Setting up Tor correctly is critical if you want to browse the dark web without exposing your real identity. A single misstep, like skipping a leak test or using the wrong browser, can undo all your privacy efforts. Follow these steps exactly to protect yourself.
1. Download and Connect a VPN
Always start by connecting to a reliable VPN. This hides your Tor usage from local networks, masks direct Tor connections, protects against network-level surveillance, and reduces the risk of being flagged for accessing privacy tools.
- Choose a nearby VPN server for better speeds and stability.
- Enable your kill switch, DNS leak protection, and IPv6 blocking (if available).
- If your ISP blocks Tor traffic or you live in a censored region, switch to obfuscated or stealth servers in your VPN app.
- Run a DNS leak test before launching Tor to make sure your real IP isn’t exposed.
2. Download and Install Tor
Download Tor from its official website at torproject.org. Avoid fraudulent Tor-like browsers that compromise your online security. The browser is free to download and works on multiple operating systems. Instructions vary depending on your operating system.
Windows
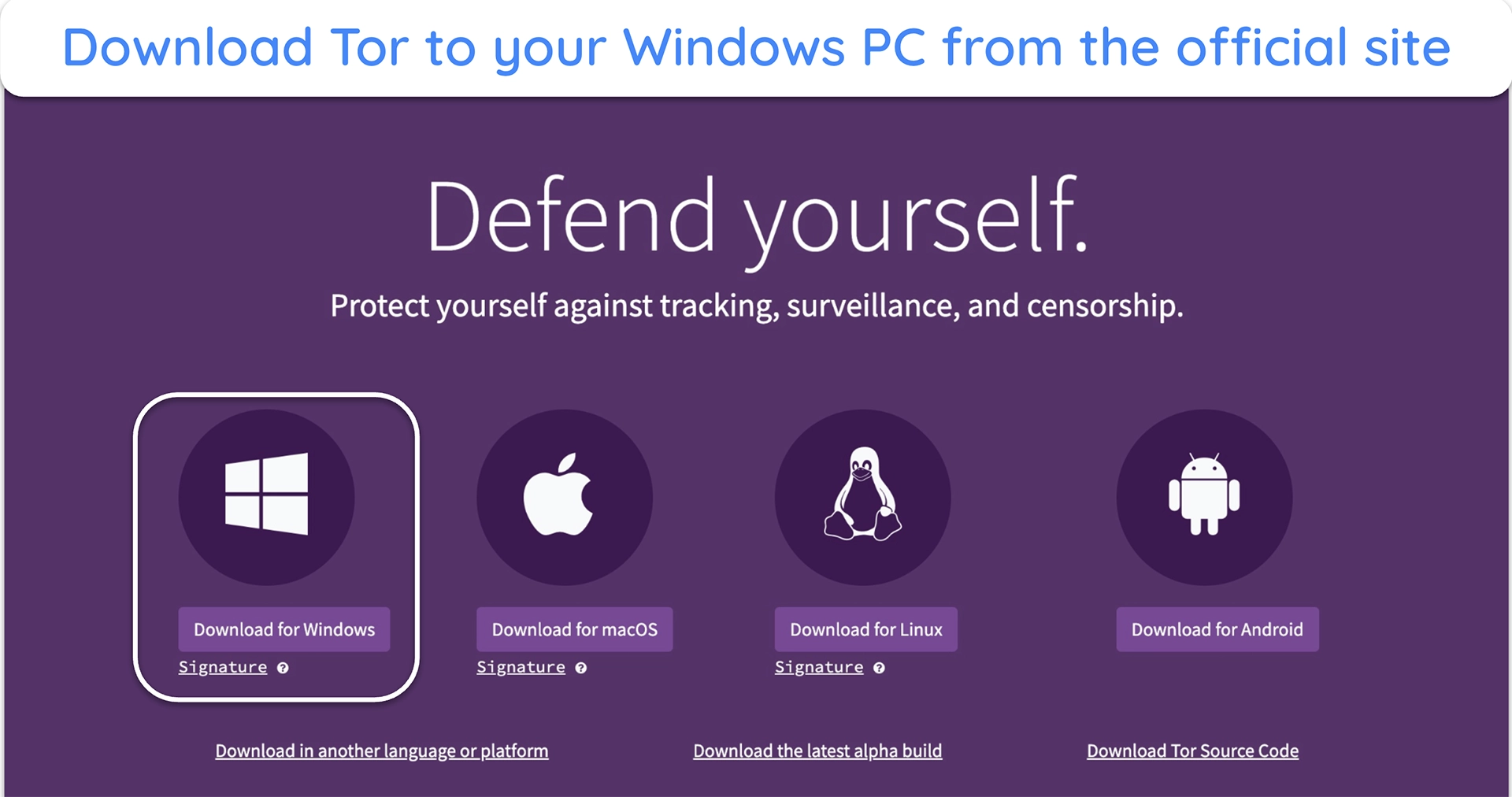
- Visit the Tor Project website and click ‘Download for Windows.’
![image of Tor Project website with "Download for Windows" highlighted.]()
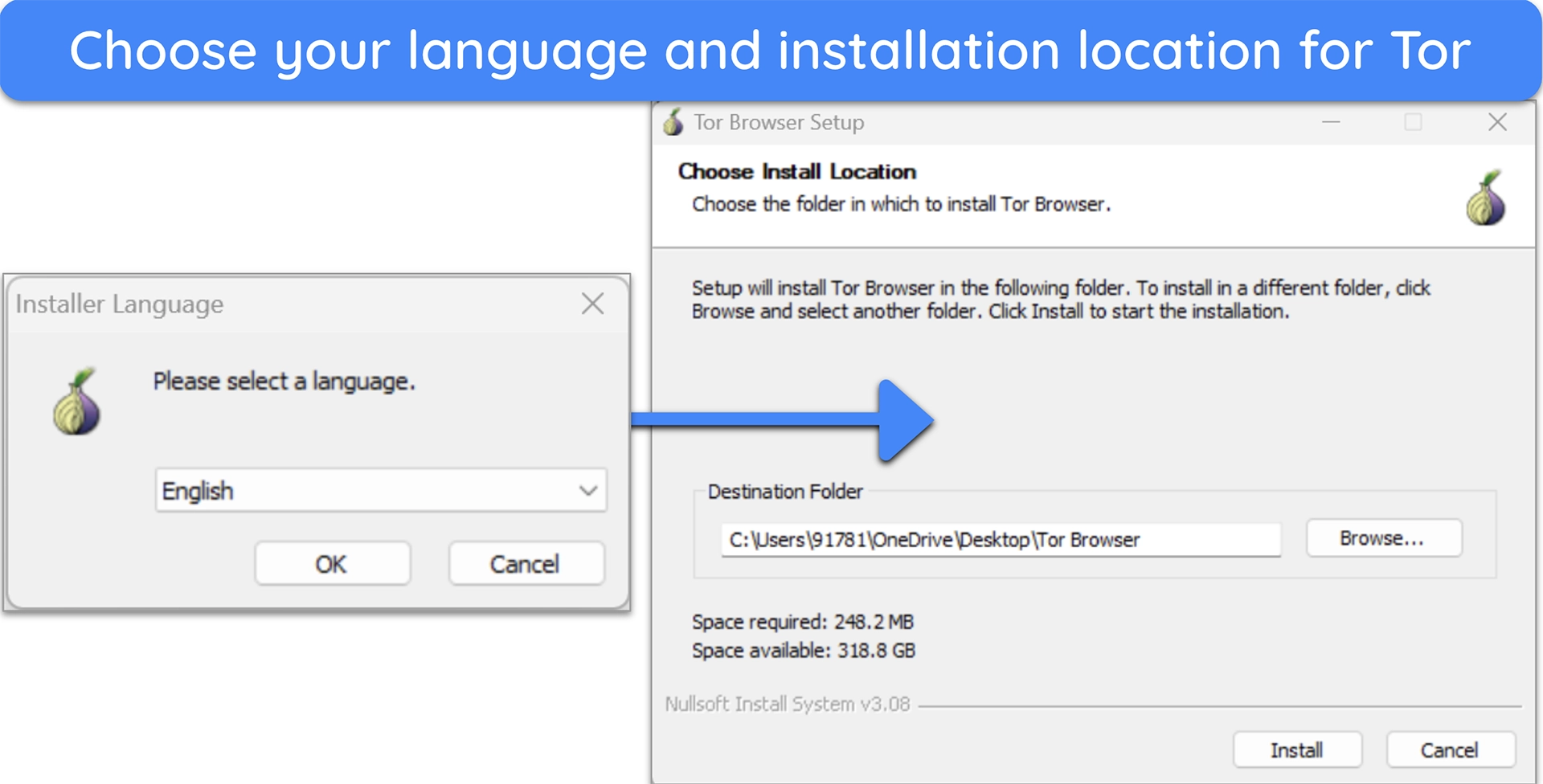
- Click the installer and follow the setup prompts. You can choose your language preference and an installation location for Tor.
![images of Tor browser setup steps for Windows devices.]()
- Click ‘Install.’ Once the installation is complete, click ‘Finish.’
- You can now launch Tor using the main menu or your desktop shortcut.
MacOS
- Download the Tor browser for Mac from the official Tor Project website. Click ‘Download for macOS.’
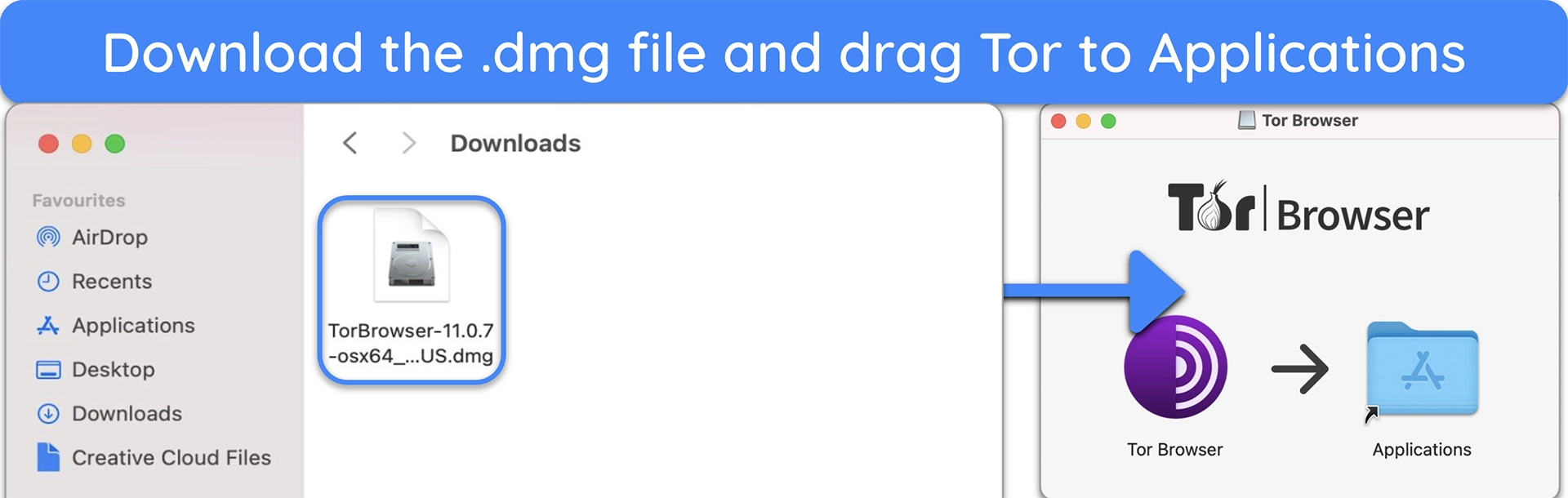
- Double-click the Tor .dmg file in your Downloads folder to install the browser.
- You’ll see a screen with a Tor icon and the Applications folder. Drag the icon into the Applications folder to install Tor.
![images of Mac with instructions showing how to download the Tor .dmg file and to drag Tor into the Applications folder.]()
- Launch Tor using the Launchpad or shortcut on your toolbar.
![image of Mac toolbar with "tor browser" in the search before being launched]()
Linux
- Download Tor for Linux from the Tor Project website.
- Right-click on the file and choose ‘Extract here.’ A new folder will be created with the extracted contents.
- Open the new folder. There will be another folder inside that you need to access called ‘Browser.’
- Double-click the Tor icon to launch the browser. You might have to confirm that you trust the downloaded application in order to open it.
Android
- Go to Tor’s official site on your Android device and tap ‘Go to Google Play.’ Only download the app from this verified source.
- Tap Install, then open the app and tap ‘Connect.’ This launches the Tor network and initializes your session.
- Once connected, visit check.torproject.org to confirm you’re on the Tor network.
iOS
- Open the App Store on your iPhone and search for Tor.
- Tap ‘Get and Install’ and wait for the browser to download.
- Launch the Tor app and tap connect.
3. Configure Tor for Privacy
Before you start browsing, open the shield icon in Tor’s toolbar and set the Security Level to ‘Safer’. This disables most scripts, fonts, and media that could expose your identity. Avoid changing default settings unless you know exactly what you’re doing.
Never install extensions or additional add-ons, even if they seem useful. They change your browser fingerprint and make you easier to track. Also, don’t resize or maximize your window. Screen dimensions are a known fingerprinting vector. The more uniform your setup, the harder it is to trace you.
4. Safely Browse and Verify Onion Sites
Opt for curated sources like Dark.Fail (PGP-verified mirrors) and Ahmia (filters abuse). Treat Hidden Wiki with caution and verify any link via multiple sources. Fake sites are everywhere, and even a one-character difference in the URL can land you on a phishing page. Always double-check URLs before clicking.
Don’t download anything unless you’re absolutely sure it’s safe. Many dark web files are laced with malware or tracking code. Don’t log into any real accounts, reuse usernames, or enter any personal details. Treat every site as untrusted unless you’ve verified it from multiple sources.
How to Stay Safe While Using the Dark Web
Even with Tor and a VPN, you’re not fully protected unless you also lock down your behavior. Most dark web leaks happen when users skip basic safety steps or reveal too much without realizing it. Use the tips below to patch common blind spots and avoid easy-to-make mistakes.
- Use a dedicated device or virtual machine — Don’t access the dark web from your daily-use laptop. Stick to a clean OS with no personal files, accounts, or background apps running. A security-focused OS for dark-web tasks like Tails is good as it routes traffic over Tor by default.
- Verify .onion URLs from multiple sources — Don’t trust single-directory listings. Double-check links on sites like Ahmia, Dark.Fail, and Reddit before opening anything.
- Avoid file downloads, even from trusted sources. Malware is often embedded in ZIPs, PDFs, or text files. If you must download, use a sandboxed environment or disposable VM.
- Avoid copying sensitive text between clearnet and Tor — Clipboard-stealing malware can capture copied data, and cross-posting can create behavioral linkages.
- Use Tor’s security level (‘Safer’ or ‘Safest’) — These modes reduce or disable risky features, including many scripts, without custom tweaks that increase fingerprinting.
- Open downloads offline — This minimizes the risk of malware “phoning home” to an attacker’s server, which could lead to data exfiltration, remote control of your device, or tracking and tracing your identity.
Tor-over-VPN vs VPN-over-Tor: The Right Order
If you’re serious about staying private on the dark web, the order in which you use your VPN and Tor Browser matters. There are two main setups: Tor-over-VPN and VPN-over-Tor. They sound similar, but they work differently:
| Best For | Pros | Cons | |
|---|---|---|---|
| Tor over VPN | Dark web access with privacy | Hides Tor from ISP, hides real IP from Tor entry node | Exit nodes can see data on non-HTTPS sites |
| VPN over Tor | Rare edge cases (not dark web) | Hides the destination IP from the Tor exit node | Breaks onion sites, adds VPN trust, ISP still sees Tor |
Tor-over-VPN (Recommended)
With this setup, you connect to your VPN first, then open Tor Browser. That means your ISP only sees encrypted VPN traffic and can’t tell you’re using Tor. It also hides your real IP address from Tor’s entry node, which is the first hop in the Tor circuit. But make sure you’re using a top, trustworthy VPN.
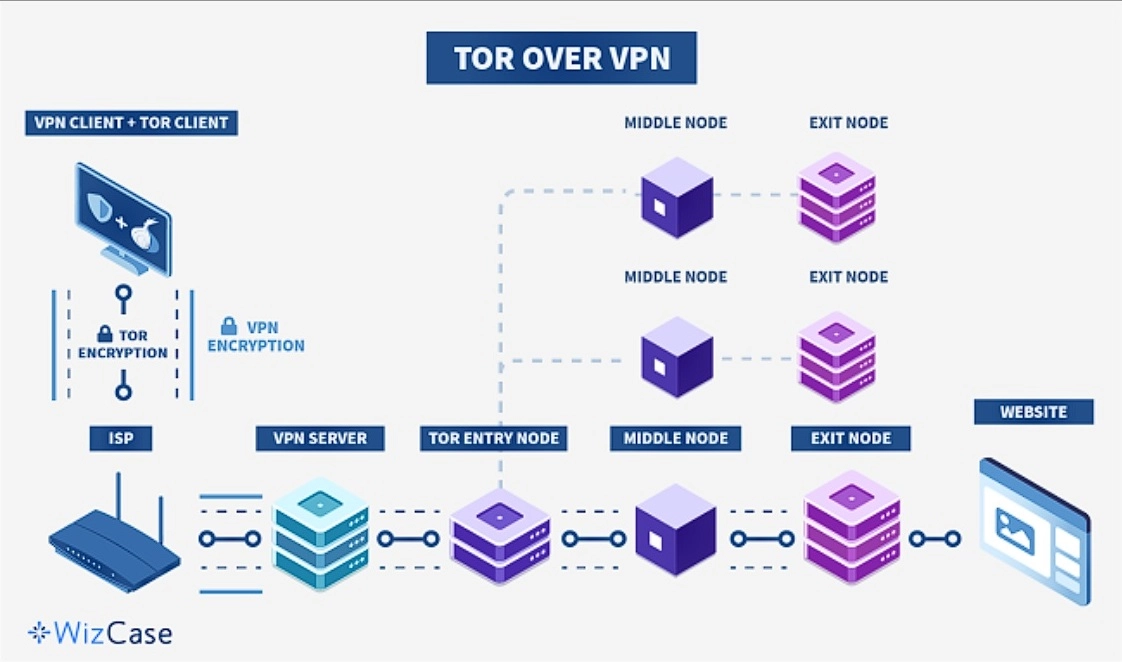
This setup is easy to configure, and you don’t need any special settings or features. Just turn on your VPN, wait for the connection to stabilize, and launch Tor. Your internet activity is still subject to exit node risks, so always use HTTPS and avoid entering any personal information on unencrypted sites.
VPN-over-Tor (Limits and Niche Uses)
This method sends your VPN connection through the Tor network. It’s extremely rare and only useful in very specific cases, like if your VPN is only accessible through Tor. With this setup, your ISP sees Tor usage, and your VPN provider sees the final traffic after it leaves Tor.
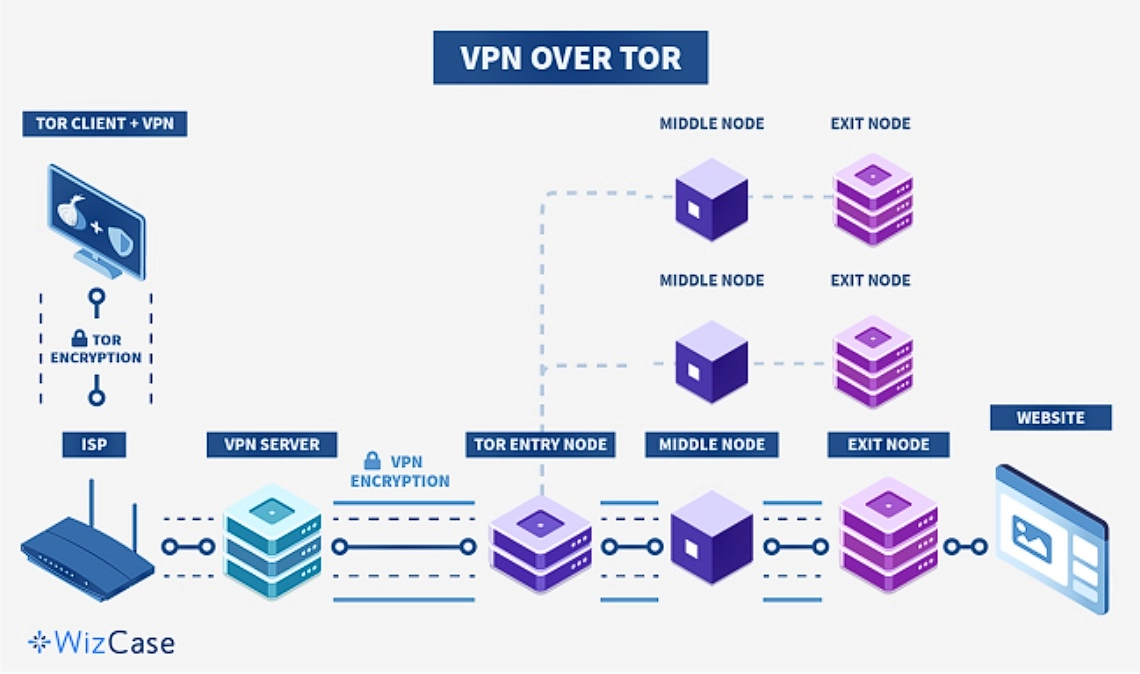
Most .onion sites won’t load this way. VPN-over-Tor breaks dark web compatibility, reintroduces trust in the VPN provider, and creates unnecessary complexity. It also adds latency and makes troubleshooting harder. For most users, this configuration does more harm than good.
Why You Need a VPN to Be Safe on the Dark Web
Tor protects your identity inside its network, but it doesn’t hide everything. Your ISP still knows you’re using Tor, and entry nodes can see your real IP address. A VPN adds protection before Tor, closing these gaps without breaking access to .onion sites.
- Hides Tor from your ISP. Your ISP only sees that you’re using a VPN, not that you’re connecting to the Tor network or accessing .onion addresses.
- Keeps your real IP off Tor entry nodes. Tor sees the VPN server’s IP instead of yours, lowering the risk of being traced by correlation attacks.
- Blocks leaks if your connection drops. A kill switch shuts off internet access the moment the VPN disconnects, preventing accidental exposure.
- Stops DNS and IPv6 leaks. A good VPN forces your device to use encrypted DNS and disables IPv6 to avoid leaking unprotected traffic.
- Bypasses firewalls and network blocks. Obfuscated servers disguise your VPN traffic, so you can connect to Tor even in places where it’s restricted.
- Protects against data retention. VPNs with a strict no-logs policy don’t store your browsing data, IP address, or connection timestamps.
Important! A VPN doesn’t encrypt traffic after it exits the Tor network. Use HTTPS, avoid logins, and never download unknown files.
The Risks and Dangers of the Dark Web
The dark web gives you anonymity, but not immunity. Most threats don’t come from the network itself — they come from the sites you visit, the files you download, and the mistakes you make. Knowing these risks ahead of time can help you avoid the most common traps.
- Malicious exit nodes — If you visit non-HTTPS sites, your data can be read or altered as it exits Tor. These nodes can inject malware, steal logins, or even redirect you to phishing pages.
- Phishing and fake mirrors — Copycat .onion sites are everywhere. Slight changes in the URL trick you into handing over your credentials or crypto to scammers posing as trusted vendors.
- Infostealers and drive-by downloads — Malware on dark sites can silently infect your device and log everything you type. Some scripts launch automatically without clicking or downloading anything.
- Correlation and timing attacks — Sophisticated attackers can match the timing of your entry and exit points on Tor. This kind of pattern analysis can link activity back to your real identity.
- Wallet drainers and crypto scams — Fake mixing services, wallet tools, and investment schemes are common. Once funds are sent, scammers drain accounts or disappear without a trace.
- Doxxing via metadata leaks — Uploading documents, using personal nicknames, or reusing writing styles can expose you. Attackers piece these clues together to unmask users.
- Law enforcement traps and monitoring — Undercover agencies run sting operations on forums and marketplaces. Even visiting the wrong place can draw attention depending on your location.
Alternatives to Tor
Tor is the most popular way to access the dark web, but it’s not the only option. Other privacy networks like I2P, Lokinet, and Freenet offer different layers of security and anonymity. Each tool works differently, and some are better suited for specific use cases than others. Here’s how they compare.
I2P (Invisible Internet Project)
I2P is a private network built for secure, anonymous communication. Instead of the onion routing Tor uses, I2P relies on unidirectional tunnels and garlic routing, which bundles multiple messages together for better traffic obfuscation. It uses its own internal DNS to access “eepsites”, not .onion addresses.
Unlike Tor, I2P is designed for peer-to-peer services like file sharing, email, forums, and even decentralized websites — all within its own closed network. Its distributed nature makes it more resistant to central points of failure.
- Best for: Anonymous internal services and P2P communication
- Limits: Can’t access .onion or regular websites; smaller ecosystem
Lokinet
Lokinet is a lesser-known but powerful alternative built on the Oxen blockchain. It routes traffic through service nodes operated by stakers in the network, creating a decentralized onion routing system that hides your IP and traffic. You can browse the regular internet or access Lokinet-exclusive SNApps (onion-style services).
Lokinet is easier to set up than I2P, and it may run faster than Tor in some cases, especially when visiting regular websites through its secure network. However, its network is still small, and there aren’t many hidden services available yet.
- Best for: Private access to clearnet or SNApps with a modern stack
- Limits: Fewer dark web sites and tools compared to Tor
Freenet
Freenet is a distributed anonymous datastore for static ‘freesites’ and files that are cached and shared across nodes. Users upload encrypted files or websites (“freesites”) that get cached and shared across the network. These freesites are static pages you can visit anonymously once Freenet loads in your browser.
Freenet is great if you want to publish or retrieve content without censorship, but not for interactive browsing. It offers 2 modes: OpenNet, where anyone can join, and Darknet, where you only connect to trusted peers. You can’t use it to access Tor or I2P links.
- Best for: Anonymous content sharing and publishing
- Limits: No live browsing; no access to .onion or clearnet sites
FAQs on Accessing the Dark Web Safely
Is it legal to access the dark web?
Can I be traced, tracked, or hacked if I use Tor?
Can my ISP see that I am accessing the dark web?
How do I find .onion websites safely?
Can I access the dark web with a free VPN?
Access the Dark Web Safely With Tor Over VPN
The dark web isn’t off-limits, but it’s not built for casual browsing. You need the right setup, a cautious mindset, and zero tolerance for shortcuts. Tools like Tor and a no-logs VPN can shield your identity, but they only work if you use them right.
If you’re planning to return, consider creating a burner OS or using a hardened Linux distro like Tails. These tools leave no trace on your device and reduce your exposure even if something goes wrong.